In our publications, we have raised the issue of privacy and anonymity when working on the Internet multiple times, as well as the issue of access to various types of services. In one of our previous articles (https://juicyscore.com/blog/en/security-vs-privacy-in-search-of-a-fair-balance-en/) we wrote about why users tend to limit monitoring of their online activity. Today we will continue the conversation about anonymity and privacy, in particular, we will talk about cases where the anonymity of the user directly or indirectly does not mean additional protection, but becomes a tool for unfair behaviour and obtaining services illegally.
There is no secret that the development of technology gives companies and financial institutions a lot of tools, including user data collection. Big business traditionally tries to collect as much information as possible about visitors of their web resources (such as web-sites or mobile apps), information about their devices and various behaviour stats in order to improve their services, to provide security / availability and to provide the maximum number of services.
Why do companies need user tracing?
Collecting a virtual user digital “trace” or digital profile allows to solve a number of problems: first of all, companies can differentiate the normal traffic created by the real client and the synthetic one; secondly, it reduces the risk of fraud and other operational risks, which are associated with the theft of personal data and digital identity; thirdly, it makes it possible to personalize settings, tips, offer details or to configure advertising in a proper way.
What are the difficulties in building a digital user profile?
In this thorough work of building the right mechanism for data collection, there are various difficulties that can be considered in two major aspects, which are essentially two sides of the same coin.
Since the parameters of the software pre-installed by the manufacturer on the device can be virtually identical for one device family, the set of parameters used to build the digital fingerprint should be as large as possible. This allows to secure differences between devices and some limited stability over time.
But if we look even more broadly, the biggest difficulty was born on the intersection of these concepts - a whole layer of software appeared, called device randomizers, the purpose of which was to impede the existing technologies for constructing the device digital profile and to show the device as new one every time. The more users notice an upward trend in the data collection, the more popular are all kinds of tools that give the user the opportunity to keep their behaviour partly private and completely anonymous. This also applies to actions on a particular resource, and even the fact of the user's presence on the site.
Excessive anonymity - where is the red line?
First of all, it is quite difficult to be sure in the privacy of the Internet in the age of information technology, although anonymity is achievable. Secondly, due to the use of certain technologies the experiences a lower speed of information downloading from various web resources and low online content rendering quality. Thirdly, such mechanisms of “anonymity” can be often in the “grey” legal zone.
The randomizers themselves can be conditionally classified as follows:
- according to the Internet connection parameters, which are randomized;
- by the method of robotization or copying the virtual users behaviour on the site and / or in mobile applications;
- by the method of randomization, when various anomalies are embedded into the digital profile of the device.
At first glance, the user's desire for excessive anonymity seems harmless, but in practice this opens up a whole layer of problems that lead to fraudulent schemes that are difficult to identify. In pursuit of unattainable privacy, which should not be confused with achievable anonymity, some unscrupulous users cross the line and, unfortunately, try to use other people's digital profiles to disguise themselves. As a result, this can lead to large losses incurred by a financial institution, which will suffer from the wave of a technically well-trained fraudulent attack.
From a technical point of view, a randomized device looks like new, as the digital profile will be tracked as different with each new entry to the site. This case, such device may be used for unlimited number of requests (for example loan applications), from some anonymous user, who in many cases pretends to be another user.
According to statistics, the share of devices with installed randomisers in the application stream is relatively small, it usually ranges from 0.1 to 1%, with possible dangerous bursts of up to 5% - 10% over a short time range.
The current statistics for different countries according to the share of devices with randomizers in the loan applications flow for Q1’20 is presented below.
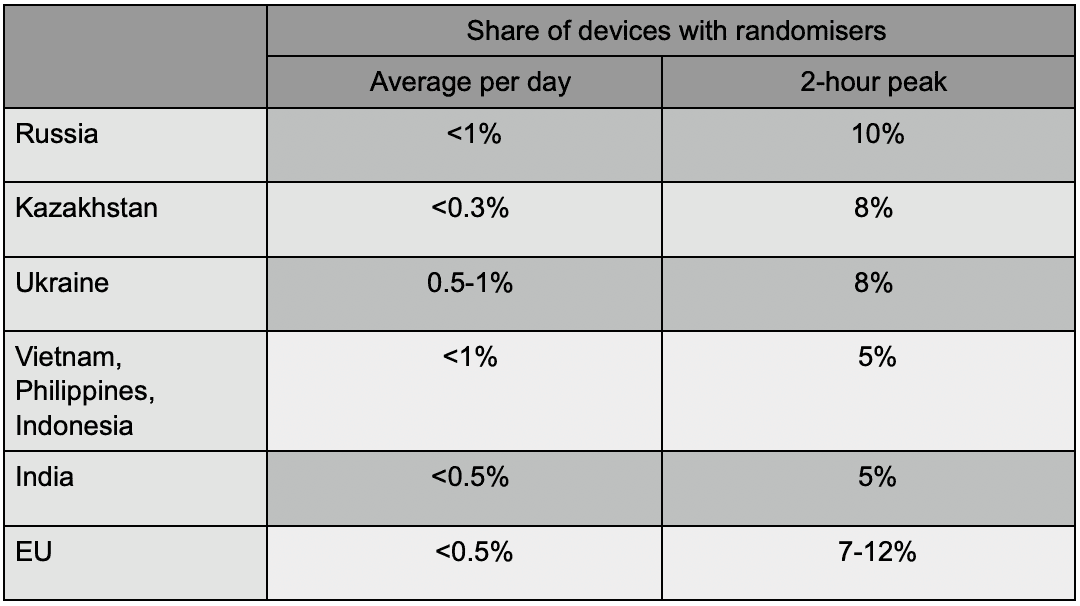
What are the main consequences of excessive privacy?
Such situation leads to two very serious consequences:
- the share of confirmed fraud risk (for example, loan default without payments and contact) is extremely high and ranges from 70 to 95%;
- at the moments of prepared attacks, the percentage of applications with randomized devices jumps from less than 1% to several percent, and tens of percent in some cases.
Thus, even the fact of using a randomizer on devices can already indicate a risk of fraud or a risk of loan default, which means it brings a danger both to a financial institution that does not want to provide a service to an unknown anonymous user with potentially unfair intentions, and to the users whose excessive suspicion and an attempt to anonymize their actions will become an obstacle to obtaining a financial service, a much needed loan or an insurance policy.
What should financial institutions do in this situation?
At the beginning of the article we briefly covered typical technological scenarios that are used to build a digital fingerprint. In order to build a digital fingerprint that is robust and stable over time and resistant to various anomalies, it is necessary to use a wide stack of device and Internet connection authentication technologies.
JuicyScore constantly monitors new randomization technologies and software in order to quickly develop and to implement respective techniques into our service and make it possible for our clients to determine these new randomisers and the level of their risk. For example, over the past month, about 10 new techniques for determining such anomalies have been into production mode.
We recommend financial institutions to conduct users digital profile multi-factor research through deep authentication methods which should not be limited to traditional and long-existing profile-building technologies and this will help to reduce the number of fraudulent activities. You should watch for reasonable anonymity, limit the use and processing of direct identifiers and real user personal data and constantly update your technological stack - this will place you one step ahead of the most sophisticated fraudulent schemes and attacks.
