Remote access technologies are very popular in the IT industry. The scenario of remote access application is quite extensive: testing programs, solving technical issues, remote work setup. However over the past few years financial institutions have seen how these technologies may do harm to both - lenders and potential borrowers: the increased growth rate of online fraud is caused not only by technologically advanced fraudsters improving their tools, but also by expansion of remote access technologies use by a wide range of individuals, including technically advanced ones and much less tech-savvy.
What are the main problems of remote access technologies?
Today we will talk about the best methods, which will help online businesses to deal with the problem of social engineering and remote access and also will shed some light on the issue of protection from these types of risk.
There is one glaring problem with remote access technologies in credit risks: they can be used by fraudsters to log in to a personal account in order to read SMS with a passcode or apply for a loan on user's behalf. In addition to that, there is an abundance of additional social problems: fraudsters usually attack socially unprotected population, for example, aged people.
Financial institutions constantly develop online channels for financial services rendering, expand the range of products and services, make their products more accessible to different categories of customers and also solve many social and economic problems associated with financial inclusion.
Being aware of this, fraudsters, in turn, improve their tools, use a combination of social engineering and remote access technologies to attack such categories of customers. Consequently, these types of attacks are often effective, so making financial institutions aware of the remote access tools on the borrower's device makes it possible to counteract such situations and reduce the number of such fraud cases.
What is a remote access technology?
Remote access technology refers to any set of IT tools used to connect, access or manage devices, resources and data stored on a local network from a remote geographic location. You may ask, so how this is different from using a cloud solution? The thing is that remote access technologies provide access to an on-premises environment rather than being hosted out of the office in a shared environment and they are accessible via the Internet. Three most common remote access technologies are Remote Desktop Services, remote access software and VPNs.
We can't but agree, remote access remains a very important tool for those companies, which have not yet migrated to the cloud or need access to on-premise computers or resources. With this access users can manage files and data stored on a remote device, it also allows them to continue to collaborate and keep a productive work from any place in the world.
Social engineering - how it works?
Social engineering is a fairly broad term that refers to a type of fraud when criminals influence a person through psychological manipulation in order to directly steal money or in order to obtain sensitive and personal data (for example, passport data, login and password from an online personal bank account) for the subsequent commission of a crime and theft of money. The main channels are social media and phone calls.
According to JuicyScore, 60-70% of professional social engineering scams follow this pattern: a user receives a call from an unknown person, who pretends to be an employee of a bank or any governmental authority. In some cases, number spoofing, call center imitation and IVR can be used. After that a scammer fraudulently lures the data, reporting false information, for example, that passwords and accounts are at risk and requests user's personal data: card details or an SMS code. Also he usually offers to download “official” bank application in order to protect user's funds. Such application is often nothing but a remote access program. On collecting victim's personal data, scammers enter personal account using remote access technologies and make a purchase, card2card transfer or apply for a loan on user's behalf.
The statistics of successful attacks performed in this way is shocking: according to our data, when a fraudster draws up a loan agreement with the withdrawal of funds to a debit card, the client gives away 2-3+ SMS or one time password codes on average.
Types of attacks
There are several types of attacks associated with the use of remote access technologies. According to our data, the first two types are the most common:
- Use of special malicious plug-ins or "prepared" browsers;
- An attack made by infected computers (most often through virus mailings, containing malicious links with dangerous programs and applications);
- Passive social engineering - when a person gives away some information during a call or installs special applications, while fraudsters do the rest;
- Active social engineering - when a person does everything with ones own hands (including the last transfer of funds or applying for a loan), and the attackers only tell the victim what to do (often they are in the office or somewhere not very far the person - they tell the victim to install malware, download the application from a link, say password from SMS and so on). This is the most difficult case to spot and to investigate as well.
How we can help to spot remote access?
As you may already know, the best way to protect personal data is not to use it. JuicyScore team is able to determine the presence of remote access technologies during the session, to be precise, directly at the very moment of filling in an application for a financial service or product obtaining.
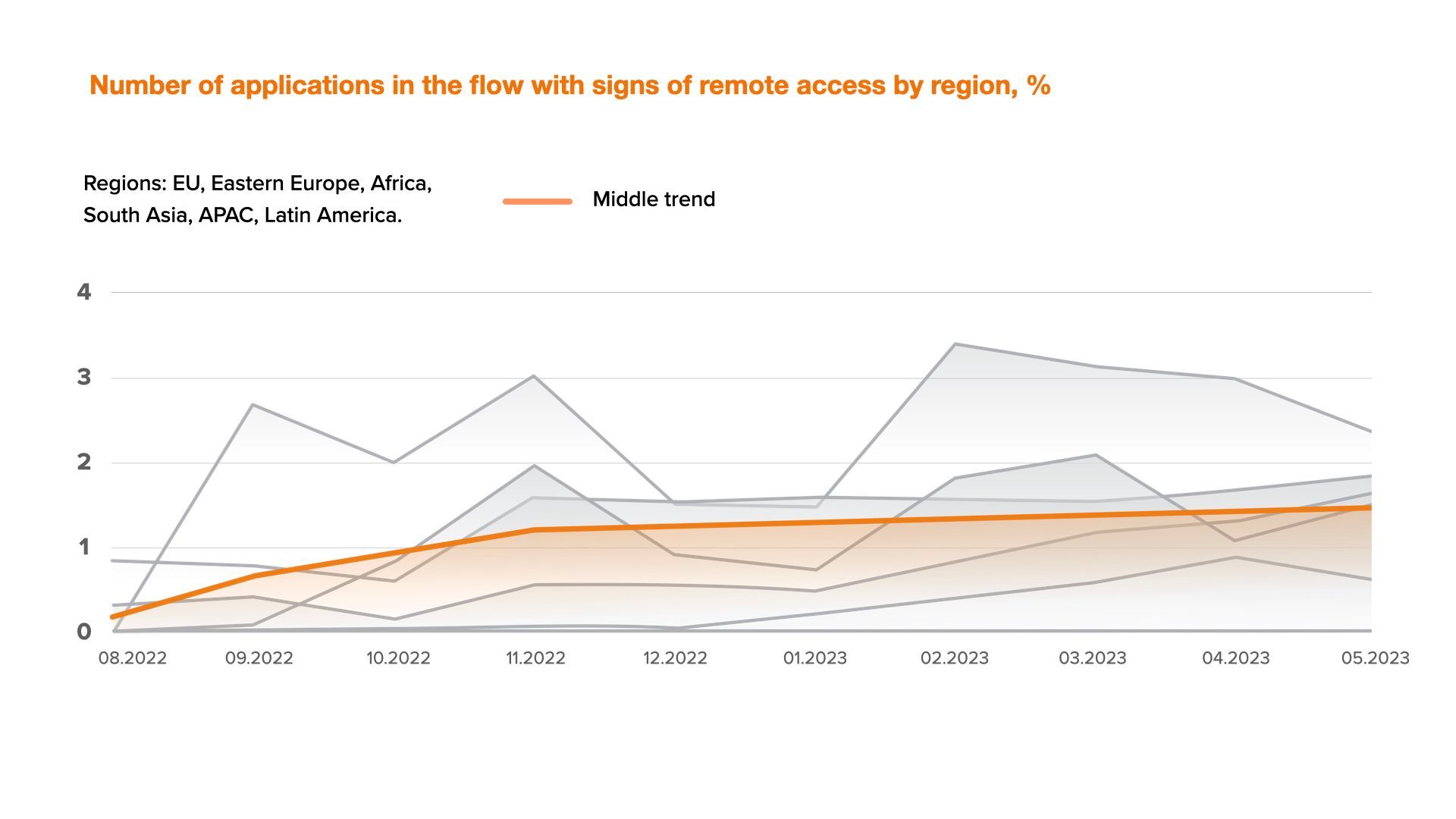
We tracked the dynamics of devices with signs of remote access we spotted recently and came to the conclusion that this indicator tends to grow.
We developed a few ways, which proved to be the best in spotting remote access technologies. They also can be effective in remote access fraudulent applications detection.
We collect as much information as possible that a browser can legally give out through different browser APIs, after that we analyze such data and identify typical signs of virtual machines or malicious plugins presence. Here are some of the features of our approach we use in order to spot remote access and social engineering:
- Dangerous plug-ins and randomizers specific to remote access spotting;
- Active dangerous applications and remote access applications on the device spotting;
- Injections during online sessions spotting;
- Specific anomalies in the traffic characteristics of the device and its connection spotting;
- Device parallel activity presence spotting.
Moreover, we are constantly discovering new tools for detecting social engineering technologies. Based on our data, we can say that the number of sessions with signs of remote access is about 2.5-3% of the total flow of applications. This fact may serve as a signal for online lenders that it is high time to pay attention to such applications and introduce additional verification.
For example, by means of repeated verification, creating pop-up warnings for users, temporarily blocking activities / conducting financially significant transactions, creating a list of allowed device prints for an existing client, comparing Device IDs or device fingerprints during registration and login, analyzing other behavioral markers. All these steps will significantly reduce the risk of fraud, which in this case may cause not only the risk of material losses for both parties, but also generally reduces trust of entire customer segments in the online channels of banks and other financial institutions.